Overview
This article provides the steps for mapping accounts from directory services, such as Active Directory or Open Directory. The mapping allows to easily administer user accounts — add, modify, remove users or groups in the LDAP database, that is applied to Kerio Connect immediately. Moreover, users can use the same credentials for Kerio Connect Client login and domain login.
Diagnosis
Mapping is one-way only. Data is synchronized from a directory service to Kerio Connect. Adding new users or groups in Kerio Connect creates local accounts.
If a directory server is unavailable, it is not possible to access Kerio Connect. Create at least one local administrator account or enable the built-in admin. Use ASCII for usernames when creating user accounts in a directory service.
To map user accounts from a directory service, please follow the steps below for:
Solution
Microsoft Active Directory
- On the Microsoft Active Directory server, install the Kerio Active Directory Extension.
- In the Kerio Connect administration interface, go to Configuration > Domains.
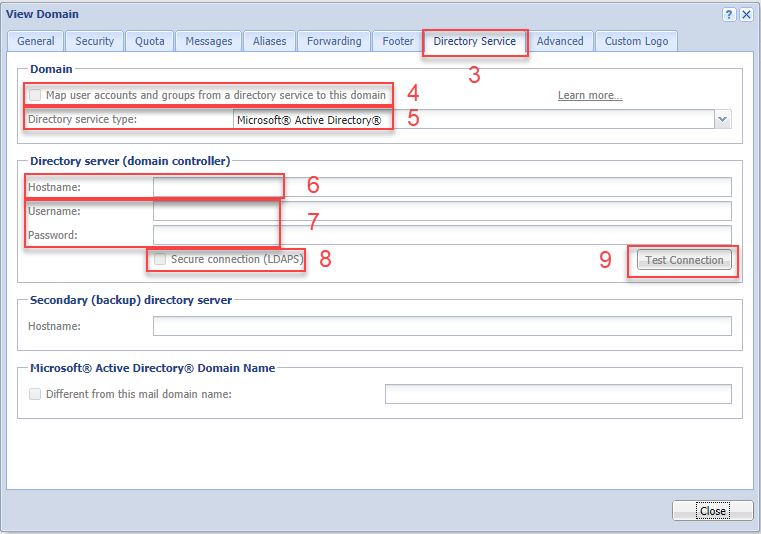
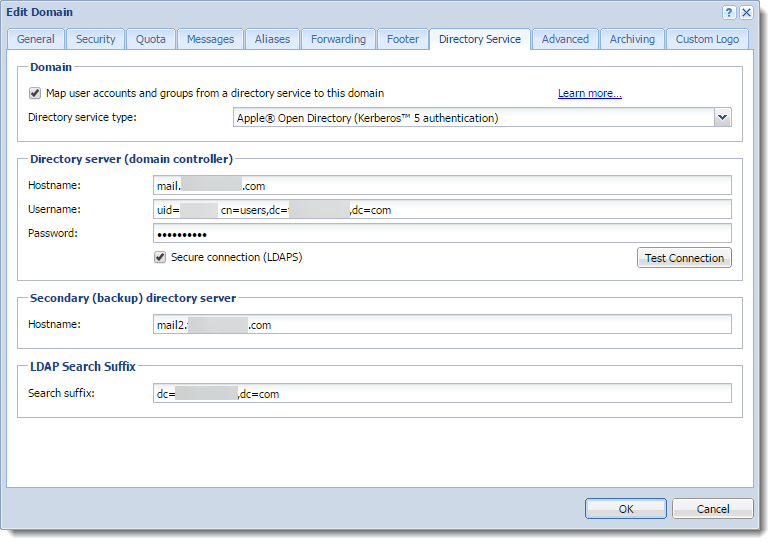
- Double-click on the required domain and select the Directory Service tab.
- Check Map user accounts and groups from a directory service to this domain option.
- As a Directory service type, select Microsoft Active Directory from the drop-down menu.
- In the Hostname field, type the DNS name or IP address of the Microsoft Active Directory server. If you are going to enable secure connection in step 8, use the DNS name.
Note: If a non-standard port is used for communication between Kerio Connect and Microsoft Active Directory, add the port number to the hostname. - Enter the Username and Password of a Microsoft Active Directory administrator with full access rights to the administration.
- (Optional) To protect data, such as user passwords (sent from Microsoft Active Directory to Kerio Connect, and vice versa), check the Secure connection (LDAPS) option.
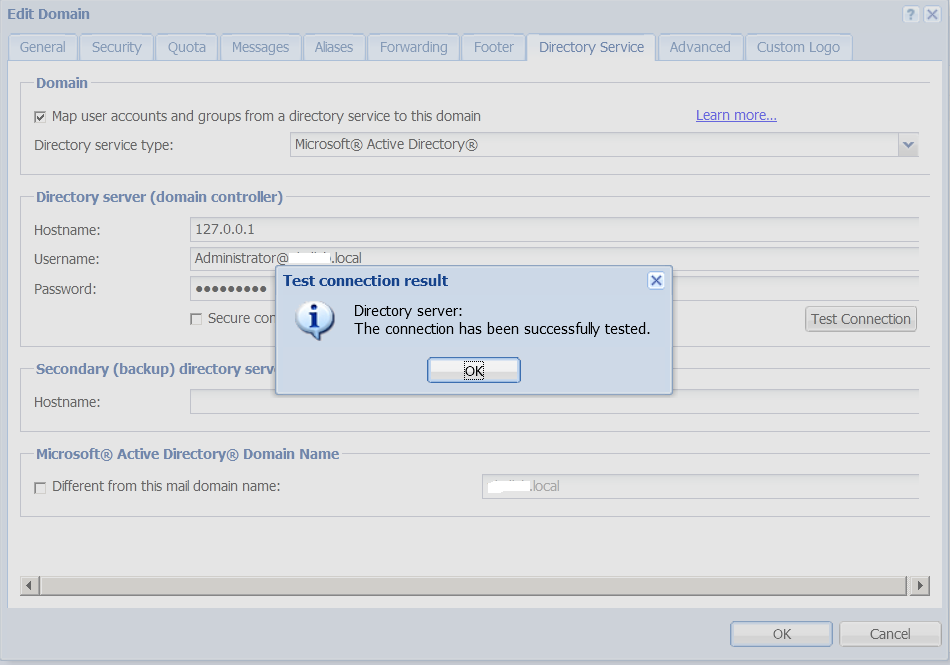
- Click Test connection to verify that you entered the correct data.
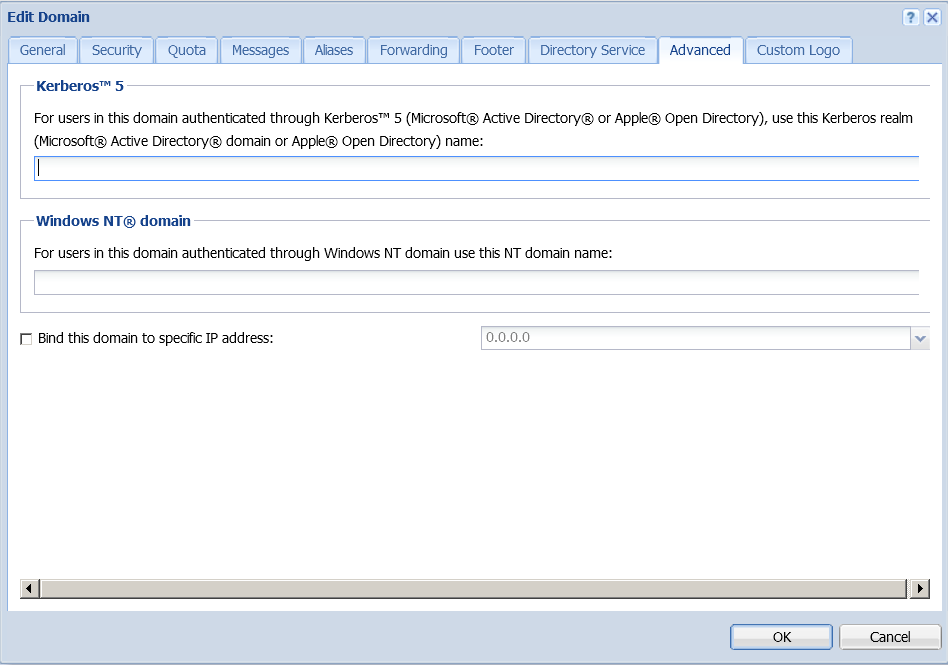
- On the Advanced tab, enter the Kerberos realm.
- Save the settings.
Apple Open Directory
- On the Apple Open Directory server, install the Kerio Open Directory Extension.
- In the Kerio Connect administration interface, go to Configuration > Domains.
- Double-click on the required domain and select the Directory Service tab.
- Check Map user accounts and groups from a directory service to this domain option.
- As a Directory service type, select Apple Open Directory from the drop-down list.
- In the Hostname field, enter the DNS name or IP address of the Apple Open Directory server. If you are going to enable secure connection in step 8, use the DNS name.
Note: If a non-standard port is used for communication between Kerio Connect and Microsoft Active Directory, add the port number to the hostname. - Enter the Username and Password of an Apple Open Directory administrator with full access rights to the administration.
- To protect data, such as user passwords (sent from Apple Open Directory to Kerio Connect, and vice versa), check the Secured connection (LDAPS) option.
- Click Test connection to verify that you entered the correct data.
- On the Advanced tab, specify the Kerberos realm.
- Save the settings.
Confirmation
Now you should be able to add Directory Service users to Kerio Connect.
Priyanka Bhotika
Comments