Overview
Kerio Connect supports configuration of SSL/TLS behavior via GUI (from version 9.4 onward) or via its mailserver.cfg file (for older and current versions). One important capability is enforcing a minimum TLS protocol version for inbound and outbound connections, including SMTP. While enforcing higher TLS levels improves security, it may block communication with servers that support only older TLS versions or none at all.
Supported protocols for enforcement include IMAPS, SMTPS, POP3, and HTTPS.
Solution
GUI Method (Kerio Connect ≥ 9.4)
-
Log in to the Kerio Connect Administration Interface.
-
Click the Configuration (gear) icon on the left.
-
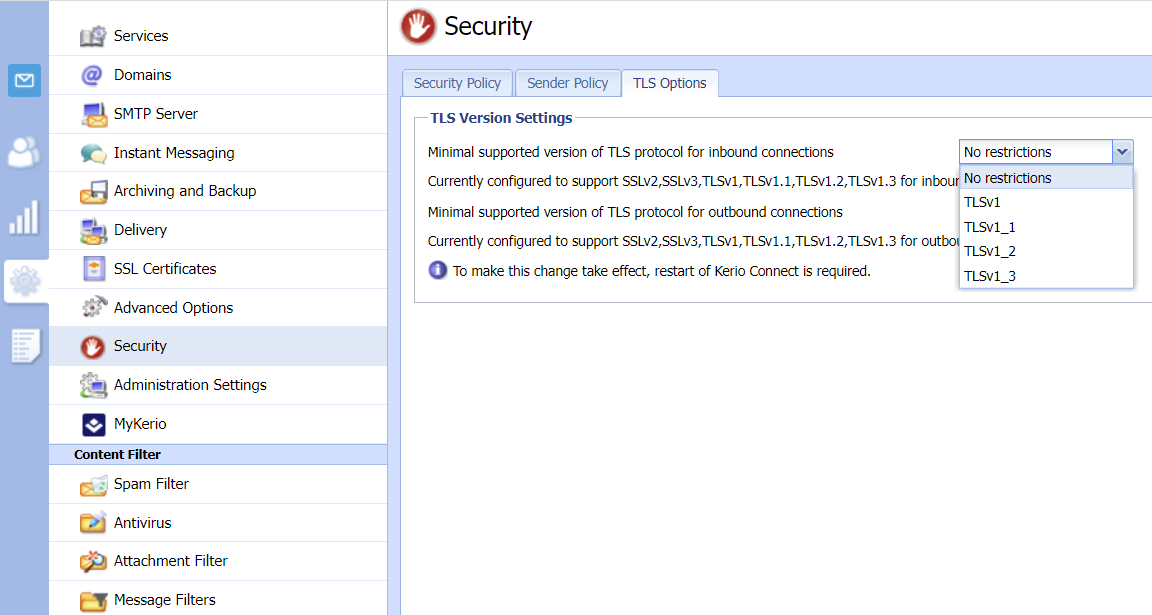
Navigate to Security.
-
Open the TLS Options tab.
-
From the drop‑down list, select the minimum TLS protocol version you wish to enforce (e.g. TLS 1.2 or higher).
-
Save changes.
This GUI option provides a simplified way to enforce TLS settings without editing config files.
Manual Method (via mailserver.cfg)
Use this approach when GUI configuration is unavailable or when you require more granular control.
-
Stop the Kerio Connect service/engine.
-
Open the
mailserver.cfgfile in an editor. (Modifying the mailserver.cfg) -
Locate the Security and SmtpSecurity sections.
-
Modify (or add) relevant TLS / cipher variables as needed.
-
Save the file.
-
Start Kerio Connect again.
If you ever want to revert to defaults, you can reset the TLS configuration by deleting those custom variable entries from the Security / SmtpSecurity sections (Resetting Kerio Connect SSL/TLS Configuration). On restart, Kerio will fall back to default values.
Key TLS / SSL Variables in mailserver.cfg
A full list of SSL/TLS configurations can be found in our dedicated Kerio Connect SSL/TLS Variables article.
Summary
-
Kerio Connect supports enforcing minimum TLS versions either via the GUI (from version 9.4 onward) or by editing
mailserver.cfg. -
While higher TLS enforcement improves security, it may block communication with servers that only support older protocols.
-
The configuration involves enabling/disabling protocols and cipher suites, and optionally controlling Diffie‑Hellman behaviors.
-
You can always revert custom TLS settings by deleting relevant variables from the config file, which causes Kerio Connect to revert to defaults.
FAQ
Q1: What happens if a remote server only supports TLS 1.0 and I enforce TLS 1.2+?
A1: Kerio Connect will refuse or fail the connection (inbound or outbound) to that server, effectively blocking communication unless downgraded.
Q2: Do I need to modify both Security and SmtpSecurity sections?
A2: Yes — Security usually handles incoming (server-side) settings, and SmtpSecurity handles outbound / SMTP client behavior. Variables should be consistent or tuned per direction. (support.kerioconnect.gfi.com)
Q3: How do I revert TLS changes if something breaks?
A3: Stop Kerio Connect, edit mailserver.cfg, remove the custom TLS variables you added in Security / SmtpSecurity, save, and restart. Kerio will fall back to default values.
Priyanka Bhotika
Comments