Overview
You have noticed a large number of suspicious email traffic on your server, with bounced emails and a larger than regular mail queue. You might see your server IP has been blacklisted, and the server is running slower than expected.
You require guidance on confirming, mitigating, and handling this potential security issue.
Solution
When you encounter any of the key symptoms above, this is often a good sign that you might be seeing issues from a compromised user account or the result of a softened security configuration on your server. When a server is exposed to a spam attack, it can lead to server freezes, overall degraded server performance, and prevent normal email flow.
It is essential to quickly verify the issue and mitigate any reputation damage resulting from spam attacks in these situations.
Verifying a Compromised Server
Kerio Connect provides a built-in method to validate the account that sends a message and where those messages originated.
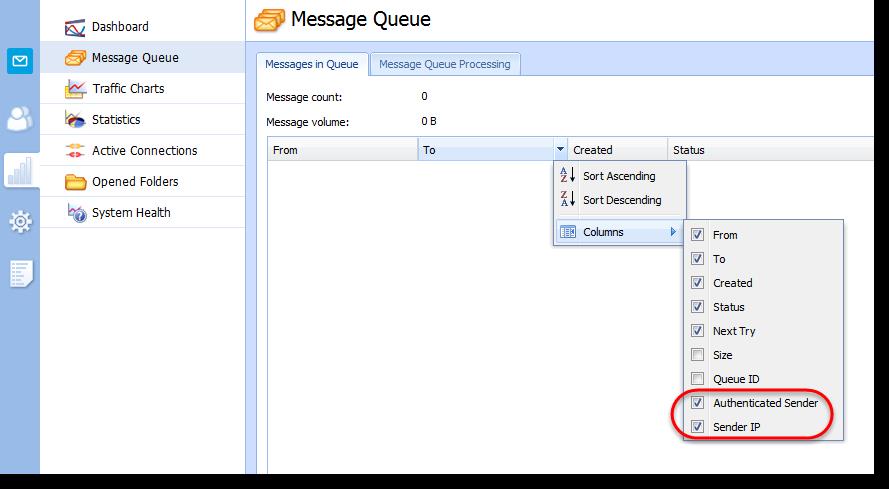
- In the administration interface, go to Status > Message Queue.
- Right-click any column header.
- Click Columns.
- Check Authenticated Sender and Sender IP.
-
Review the messages within the queue using the guidelines below:
- The Authenticated Sender can indicate that a user’s password may have been compromised.
- The Sender IP can indicate if the email was sent internally (this can point to a virus or a Trojan on a local user machine) or externally (this suggests a guessed password of an authenticated user). For example:
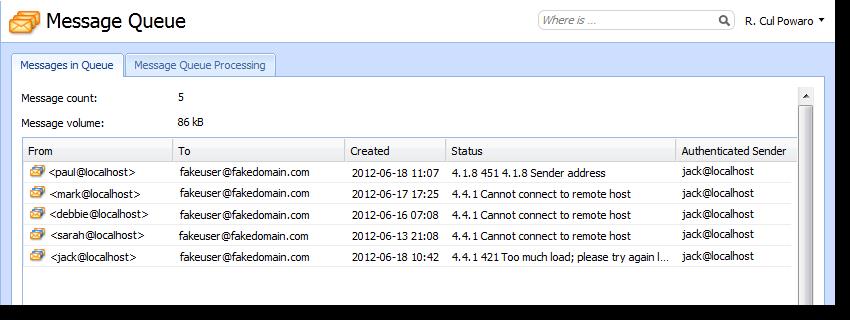
This message queue shows:
- The From address is continually changing.
- The Authenticated Sender is always jack@localhost. This could indicate that Jack’s password has been compromised/guessed.
Mitigating the Issue
If you identify the above behavior within the messages filling the queue, it is highly recommended that you act on the steps below to secure your environment.
- We suggest that you enforce a change of all user passwords as a precaution. At a minimum, change the password of any users identified using the guidance above.
- Perform a Virus/Malware scan on any machines that the affected users have accessed.
-
Stop the Kerio Connect Server to terminate any existing connections and Manually clear the mail queue.
- It is suggested that you retain the emails within a temporary “example.old” folder to avoid losing any legitimate emails during this process.
- Once the issue is confirmed as mitigated, you can take steps to review and re-insert any legitimate emails manually.
-
Once the queue folder has been cleared, Start the Kerio Connect Server.
- Note: If the Kerio Connect Server does not start, restart the Host Server machine directly.
-
Monitor the now cleared Mail Queue and confirm that no further spam messages appear.
-
If you continue to see suspicious messages appearing, this often indicates that you may have other exposed vectors, such as unexpected inclusions within your IP Address Exception Groups.
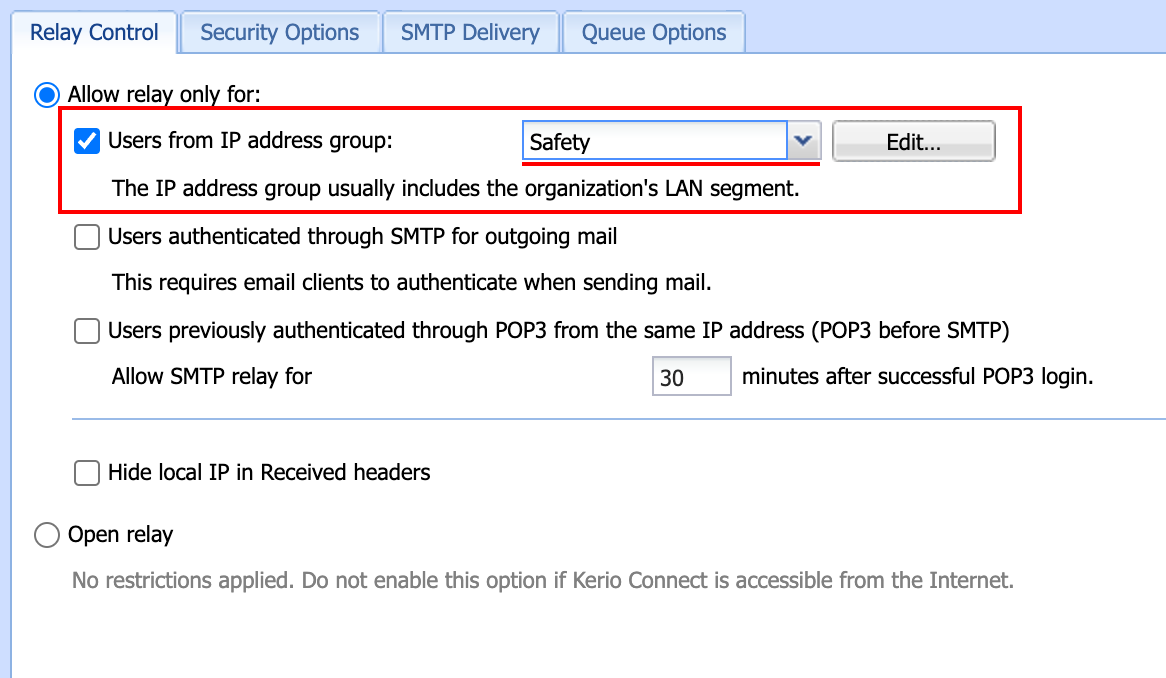
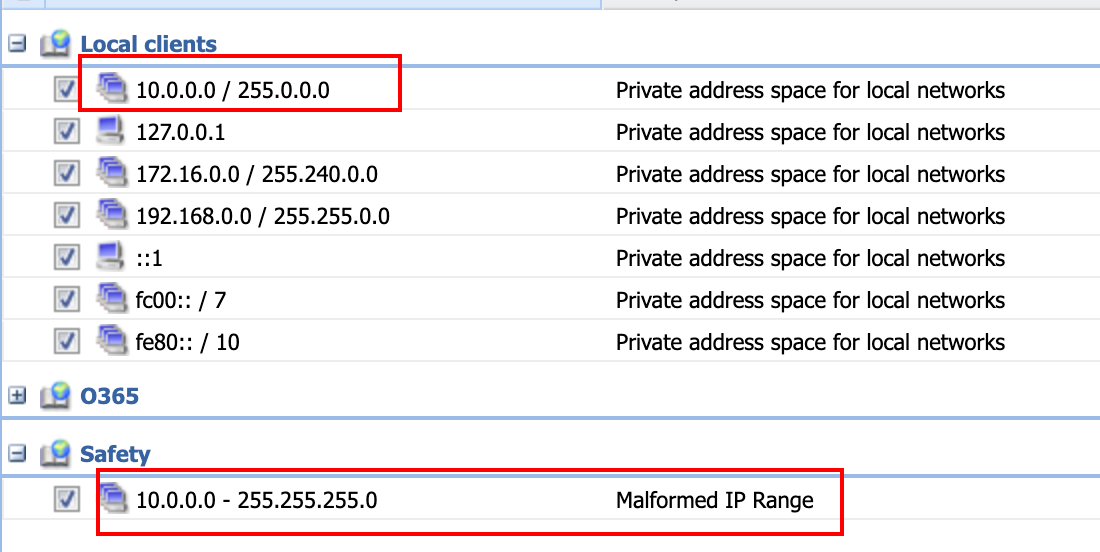
- For example, here we see an attempt to establish a local IP Mask, but accidentally creating a fully open IP Range in error:
- For example, here we see an attempt to establish a local IP Mask, but accidentally creating a fully open IP Range in error:
-
Review the following menus within the WebAdmin to confirm which IP Address Group is assigned to the various Security Exception lists:
- Security > Security Policy
- Security > Sender Policy
- SMTP Server > Relay Control
- SMTP Server > Security Options
- Spam Filter > Blacklists
- Once you identify the IP Group used within the sections above, you can make the necessary adjustments within Configuration > IP Address Groups.
- Once any malformed ranges or suspicious IP addresses have been adjusted, repeat the steps above to restart and clear the mail queue to confirm that no further messages appear.
-
If you continue to see suspicious messages appearing, this often indicates that you may have other exposed vectors, such as unexpected inclusions within your IP Address Exception Groups.
-
Once you confirm that no further Spam messages are being generated or queued within your server, it is suggested that you review any potential reputation damage:
- Various Sender/IP score reputation services help to identify Blacklisting. The most common are:
- You can also use a service like MxToolbox to check your domain against several blacklists at once and provide guidance on getting unlisted.
- In some exceptional cases, your IP address’s reputation may be heavily impacted by the spammers. As the spamming does not originate from Kerio Connect, the solution may be to change the public IP address so that the server is no longer associated with the malicious sender. The sender will probably continue using the same IP to send spam emails, but it will no longer be linked to your mail server.
Preventative Measures
While the steps above can help address issues that arise, the best policy is to ensure that your Mail Server is secured before a problem appears.
-
Configuring Essential DNS Records for Spam Protection
- Most importantly, setting up Sender Policy Framework(SPF) records for your domain helps ensure that spammers cannot spoof your email domain when sending email to servers that perform SPF or Caller ID record lookups. (A standard security measure)
- Setting up PTR(Reverse DNS lookup) and DKIM records with your DNS hosting provider can provide additional authority to messages sent from your server, alleviating potential blacklisting scenarios.
-
Hardening your current Security Configuration:
-
Improving User Account Security
- Preventing Password Guessing Attacks using the built-in security settings can avoid compromised accounts before they occur.
- Requiring Complex Passwords and enforcing users to change their passwords regularly can be configured directly within the Domain settings.
- For Servers running v9.4 or later, you now have access to 2FA and Application Passwords which can provide further security.
-
Improving Kerio Connect Security
- Securing Kerio Connect and Securing the Kerio Connect SMTP Server provide an overview of all of the enhanced security features available directly within the WebAdmin configuration settings.
- Configuring AntiHammering in Kerio Connect can help prevent spamming by defining a limit that blocks frequent SMTP logins by suspicious IP addresses.
- If you are not already making use of these features, it is suggested that you review these and consider enabling them.
-
Improving Network Security
- This adjustment is outside of the scope of Kerio Connect Support’s ability to help, but that does not mean it is any less important.
- We recommend that you implement an appropriate network-level firewall and IPS solution to help prevent malicious traffic before it ever reaches your Mail Server.
- Please discuss this further with your IT Team to determine the options available to you.
-
Improving User Account Security
Priyanka Bhotika
Comments