Overview
Kerio Connect has a built-in AntiHammering security feature that protects from frequent SMTP logins by suspicious IP addresses. Once the failed login limit is reached, the Kerio Connect blocks the IP address, which makes it impossible for devices (Apple macOS) to log in. The same problem may occur for IMAP, POP3, HTTP services.
Security logs generate similar errors:
[17/Nov/2023 11:31:00] SMTP: User user1@example.com doesn't exist. Attempt from IP address x.x.x.x.
[17/Nov/2023 11:31:01] SMTP: User user2@example.com doesn't exist. Attempt from IP address y.y.y.y.
[17/Nov/2023 11:31:07] Failed SMTP login from suspiciousdomain1.com with SASL method LOGIN.
[17/Nov/2023 11:31:08] Failed SMTP login from suspiciousdomain2.com with SASL method CRAM-MD5.
[17/Nov/2023 11:31:08] SMTP: AntiHammering - IP address x.x.x.x will be blocked for 5 minutes, too many failed logins from this IP address.
[17/Nov/2023 11:31:08] SMTP: AntiHammering: connection from IP address x.x.x.x is blocked
Prerequisites
Administrator (root) access to the Kerio Connect server
Diagnosis
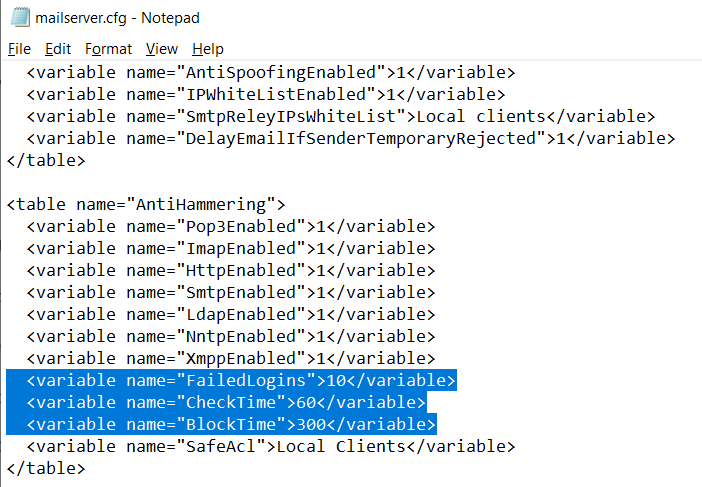
By default, Anti-Hammering is enabled for all standard Kerio Connect services, such as POP3, IMAP, HTTP, SMTP, LDAP, NNTP, and XMPP. The Anti-hammering checks the failed login attempts during 1 min period and if the limit of 10 is reached, the reported IP address is being blocked for the next 5 minutes. The IP addresses can be excluded from the Anti-hammering check by specifying the SafeAcl variable.
All these options can be changed by modifying mailserver.cfg file.
Solution
- Stop the Kerio Connect service.
- Navigate to the Kerio Connect installation folder. Defaults are:
- Windows: C:\Program Files\Kerio\MailServer
- macOS: /usr/local/kerio/mailserver
- Linux: /opt/kerio/mailserver
- Open mailserver.cfg and locate the AntiHammering table. Modify the necessary limits:
- FailedLogins - number of login failures for specific service, i.e. SMTP. The default value is 10.
- CheckTime - the time period to check the same IP address. The default is 60 seconds.
- BlockTime - the duration of IP address blocking. The default is 300 seconds.
- (Optional) Modify per service variables to disable specific protocols, i.e. setting Pop3Enabled to 0 (zero) will disable the Anti-hammering protection for POP3 service.
- Start the Kerio Connect service.
Confirmation
The Anti-hammering limits are set to the custom values.
Priyanka Bhotika
Comments